

Retrieved 15 May The FAQ section of the TrueCrypt website states that the Trusted Platform Module TPM cannot be relied upon for security, because if the attacker has physical or administrative access to the computer and you use it afterwards, the computer could have been modified by the attacker e.
TrueCrypt documentation states that TrueCrypt cannot secure data on a computer if it has any kind of malware installed. Note that your submission may not appear immediately on our site.
CSipSimple Jitsi Linphone Ring Zfone. Gribble; Tadayoshi Kohno; Bruce Schneier 18 July So it appears that the unexpected putting it mildly disappearance of TrueCrypt.
Error 405 Not allowed.
Downloads written by admin on July 29, average rating 4. But readily browsable if someone wishes to poke around within the source with their web browser. Several versions and many additional minor releases have been made since then, with the most current version being 7. This is the home of the TrueCrypt auditing project.
Retrieved 14 March A just launched, Swiss-based, possible new home for TrueCrypt.
TrueCrypt
If a system drive, or a partition on it, has been encrypted with TrueCrypt, then only the data on that partition is deniable. Additional online TrueCrypt sites and repositories: Home Documentation Downloads Screenshots FAQ About License Impressum Partners. In October , British—Finnish activist Lauri Love was arrested by the National Crime Agency NCA on charges of hacking into a US department or agency computer and one count of conspiring to do the same.
The company states that with those products, SecurStar "had a long tradition of open source software", but that "competitors had nothing better to do but to steal our source code", causing the company to make its products closed-source , forcing potential customers to place a substantial order and sign a non-disclosure agreement before being allowed to review the code for security.
To prevent those, the documentation distributed with TrueCrypt requires users to follow various security precautions. History of cryptography Cryptanalysis Outline of cryptography.

Their true final version, 7. Retrieved 17 June As the audit moves into its next phase, digging past the startup and boot loader and into the core crypto, updates will be posted and maintained here. This page was last edited on 19 July , at This led the TrueCrypt Team to immediately stop developing and distributing TrueCrypt, which they announced online through usenet. Suddenly, for no disclosed reason, we should no longer trust it?
- There will be continuity.
- Archived from the original on 5 February Retrieved 25 January
- Protect Your Data With Encryption. UC Browser - Fast Download.
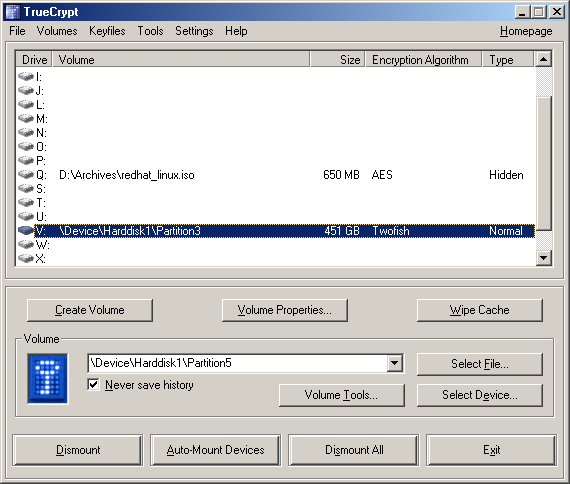
It is truly lovely. Individual ciphers supported by TrueCrypt are AES , Serpent , and Twofish.

This audit "found no evidence of deliberate backdoors, or any severe design flaws that will make the software insecure in most instances. Archived from the original on 30 May TrueCrypt is vulnerable to various known attacks which are also present in other software-based disk encryption software such as BitLocker.
Truecrypt
Retrieved 29 May Given the deliberate continuing licensing encumbrance of the registered TrueCrypt trademark, it seems more likely that the current TrueCrypt code will be forked and subsequently renamed. July 29, by admin. Indeed, it will not be easy. Reviews News Video How To Smart Home Cars Deals CNET Home Reviews at Guide.
- Automatically and transparently encrypt in real time.
- The header key and the secondary header key XTS mode are generated using PBKDF2 with a bit salt and or iterations, depending on the underlying hash function used.
- TrueCrypt answers yes to both.
Thank You for Submitting Your Review,! Archived PDF from the original on 30 December



[MYCB(RAMBLER)FREETEXT-1-2
[MYCB(RAMBLER)FREETEXT-1-2
[MYCB(RAMBLER)FREETEXT-1-2
[MYCB(RAMBLER)FREETEXT-1-2